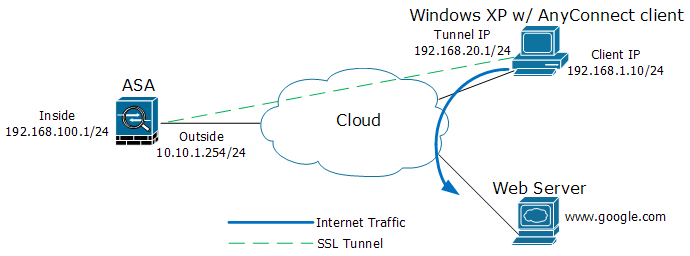
This post is a guide to configure a Cisco Adaptive Security Appliance (ASA) device to perform remote access SSL VPN with the stand-alone Cisco AnyConnect VPN client. I followed a few tutorials on the web (including a couple of examples from the Cisco website), but I failed to implement a complete solution. The following recipe has been thoroughly tested and verified.
Ingredients used for this post:
- Cisco 5500 Series ASA with software version 8.0(2)
- Cisco AnyConnect SSL VPN client version for Windows 2.3.0254
1. Copy AnyConnect package to the Cisco ASA device.
copy tftp flash
192.168.100.30
anyconnect-win-2.3.0254-k9.pkg
2. Create an IP address pool.
conf t
ip local pool VPNPOOL 192.168.20.1-192.168.20.100 mask 255.255.255.0
3. Enable and configure WebVPN.
webvpn
enable outside
svc image disk0:/anyconnect-win-2.3.0254-k9.pkg 1
tunnel-group-list enable
http redirect outside 80
svc enable
4. Create access-list entries that allow traffic between the inside and remote users and also an entry for the split tunnel.
access-list VPN-EXEMPT-NAT permit ip 192.168.100.0 255.255.255.0 192.168.20.0 255.255.255.0
access-list SPLIT-TUNNEL standard permit 192.168.100.0 255.255.255.0
5. Verify the sysopt command is enabled.
sysopt connection permit-vpn
6. Configure a group policy.
group-policy CLIENTGROUP internal
group-policy CLIENTGROUP attributes
dns-server value 192.168.100.10
vpn-tunnel-protocol svc
group-lock value SSLGROUP
split-tunnel-policy tunnelspecified
split-tunnel-network-list value SPLIT-TUNNEL
webvpn
svc keep-installer installed
svc rekey time 30
svc rekey method ssl
svc ask none default svc
7. Create a new user account.
username ssluser1 password ssluser1
8. Configure a tunnel group.
tunnel-group SSLGROUP type remote-access
tunnel-group SSLGROUP general-attributes
address-pool VPNPOOL
default-group-policy CLIENTGROUP
tunnel-group SSLGROUP webvpn-attributes
group-alias SSL-VPN enable
9. Configure PAT and enable NAT exemption for the VPN clients.
global (outside) 1 interface
nat (inside) 1 0.0.0.0 0.0.0.0
nat (inside) 0 access-list VPN-EXEMPT-NAT